General
This document describes ways of improving security and protecting your system from fraud.
Listed is an overview of Sippy's current security features:
- Complex passwords - default password template is a minimum of 7 alphanumeric digits. Password templates are customized by on a per-account basis by our support team.
- Password Strength indicator - Password strength is shown to users when user passwords expire or are created for the first time (Starting in 5.2).
- Multi Factored Authentication - Switch operators can enable multi-factored authentication for web users. Users will have the option to use an email based system or google authentication (Starting in Sippy 2020).
- SSL Certificates - SSL certificates can be generated from the softswitch via Let's Encrypt. This is a free service if you have a domain name assigned for your softswitch. Users can still upload their own SSL certificates for their system.
- Encrypted passwords - passwords are encrypted when saved and cannot be retrieved from the database.
- Separate VoIP credentials for Digest Authentication - different web and SIP traffic credentials for Accounts, accessibility and user security.
- Sophisticated VoIP traffic Authentication - Combined Remote IP, Incoming CLI and Incoming CLD authentication to authenticate traffic to an Account.
- Account session limits - Total session limits (inbound/outbound combined) protect each Account from traffic flooding resulting from Account hacking.
- Account CPS limits - CPS limits protect an Account from traffic flooding that results from hacked Accounts.
- Account Balance token system - Real-time Account's Balance apply logic to incoming call attempts referencing remaining Balance/Credit, calls cost/rate, and calls in progress to allow additional calls to pass.
- Built-in Firewall for additional network security layer - Web, SSH, DB, and SIP traffic firewall rules.
- Web Access Control restriction - restrict staff web login to specified IP addresses/locations.
- User Audit logs - Monitor changes made by staff and track when they access the softswitch and from where.
- Connection channel and CPS limits - restrictive routing and capping of calls to specified upstream locations.
- Adjust a default password_policy template - to adjust, request that the support team provides you the default parameters that your system uses and adjust them if needed.
- In-house framework (Sippy B2BUA & RTPproxy) ensures Sippy is not remotely vulnerable to industry-wide security and fraud attacks.
- Proper ACD value set in tariff, with the ACD=Max session time, the system will never push an Account's or Customer's balance below zero, a drawback of this security feature is that it can result in some calls being dropped.
- Transparent external firewall is recommended for handling complicated rules and to protect an overload of the network card from fraudulent traffic/packets or any DDOS attack.
- Use PINs for vouchers if they are used.
- Use PINs for accounts if calling cards are used.
- Avoid using authentication rules with only CLI/CLD, the IP address adds extra security to the authentication.
- Use authentication by Vendor/Connection in the DID authentication rules if DIDs are used in the scenario.
- Mask topology of your network using the media relay feature that proxies the RTP and hides the original IP of a device.
- Use your own VPN server if your staff is seating on a dynamic IP. Such an approach would make connection to the Sippy server more secure, allow you to configure a web firewall, and restrict suspicious attempts from accessing the web/db/ssh from unknown IPs.
- In-house framework (Sippy B2BUA & RTP Proxy) ensures Sippy is not remotely vulnerable to industry-wide security and fraud attacks.
Steps to take to secure your Sippy Softswitch:
Feature | Location | Note | Document | |
1. | Complex passwords | My Preferences > Web Password My Staff > Users > User's parameters | User password leaking is the number 1 cause of fraud across all forms of software. Set significantly complicated passwords for your users to prevent unauthorized access. | |
2. | IP Firewall | System Management > Tools > Ip Firewall | Prevent unwanted traffic or hacking attempts through SSH, SIP, Web, and DB firewall configuration. | See below for simple configuration guidelines. |
3. | External Firewall (if required) | External service. | Configure an external firewall in front of Sippy to help prevent DDoS attacks, port scanning etc. This is a network application. | External Firewall setup for use with Sippy Softswitch |
4. | Web Access Control | Profile > My Preferences My Staff > Users > User's parameters | Restrict access to the Sippy Softswitch through User accounts by configuring your IP's into the web access control field. Only operators from the specified IP will gain access to your switch. | See below for simple configuration guidelines. |
5. | Overdraft protection | Billing > Tariff > Average Call Duration | Sippy passes calls based on a balance token system that is governed by the Average Call Duration on Tariff. Longer Average call Duration will result in fewer calls passing when an Account's balance is low. | |
6. | SNMP monitoring traffic flagging. | External service. | Configure an SNMP application as an external service to monitor and alert to traffic spikes and unwanted access attempts. | Using SNMP to monitor Sippy Softswitch statistics |
The Sippy softswitch has been developed with security features that are in line with our goal of producing the most secure softswitch on the market.
Web access control
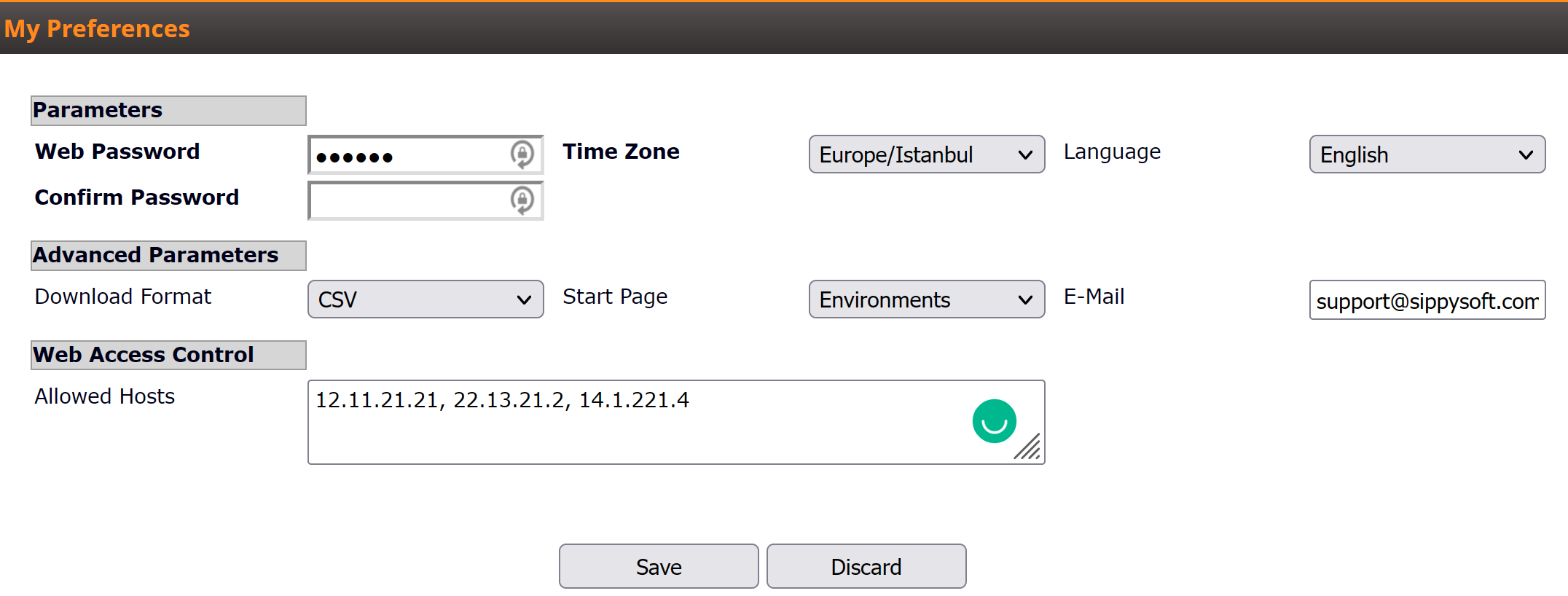
The Web access control feature allows a Sippy softswitch owner to specify the exact list of IPs for web access. Each particular web-user can be specified in the "My Preferences" menu of the Customer or web user. Thus, only listed IPs are able to login to the web with the credentials of that user.
By default the owner will see the value "Any" in the "Allowed Hosts" field. "Any" means that anyone can access the web interface with the proper login and password. You can specify a list of IPs with comma separated values; in this configuration, only clients from the list or IPs would be able to login to the web interface provided that they have the proper login and password.
In "My Preferences" of your own user:


In "System Management" -> "Users" section:

IP Firewall tool
The IP firewall tool allows you to restrict access to the database, web interface, SSH or SIP traffic from static IPs. You can add rules to the firewall list in the following menu: "Tools" > "IP Firewall" (see screen-shot for your reference).
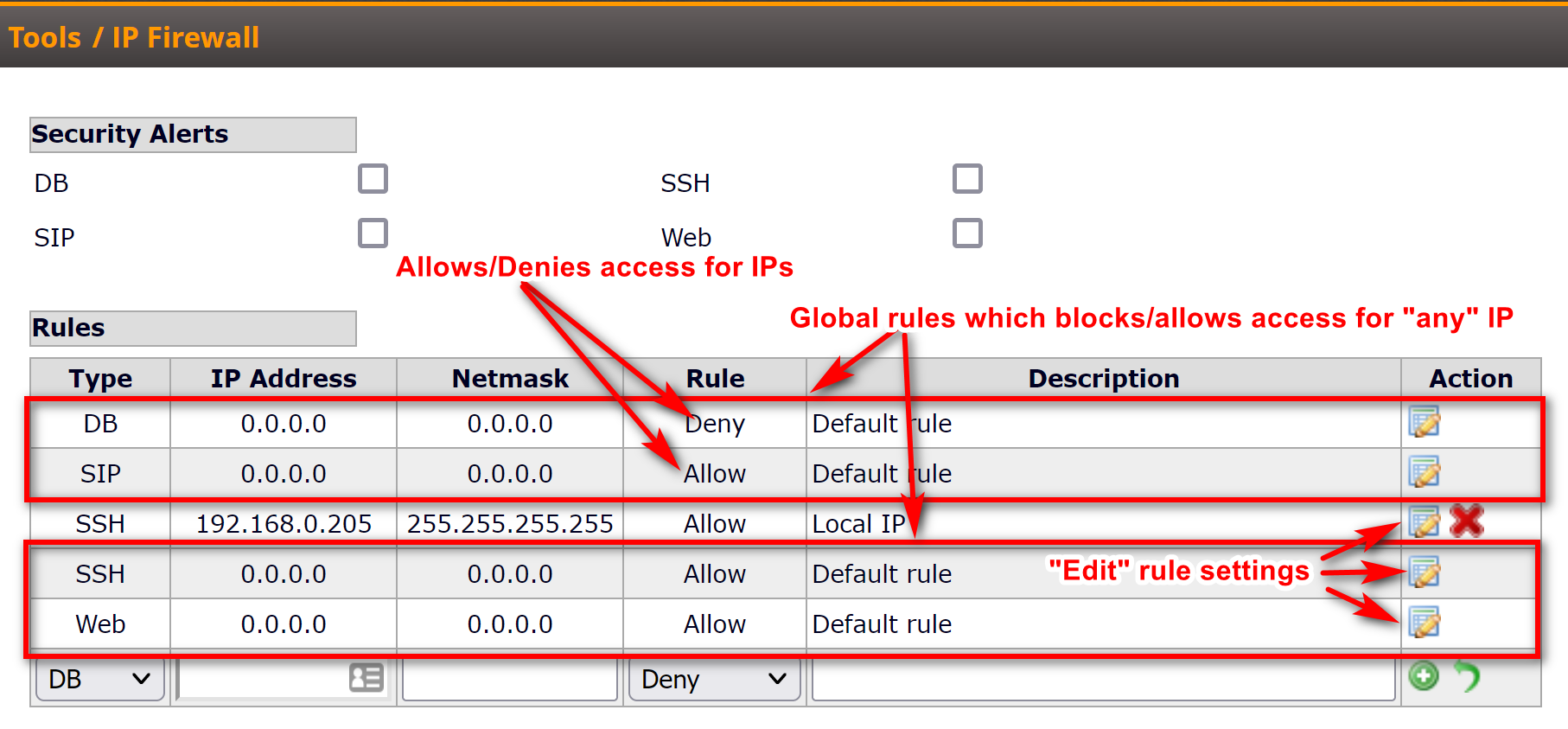
The IP firewall can be configured only for static IP addresses. Also, note that the netmask should be 255.255.255.255 if you want to block or allow only one particular IP address. In case of a dynamic IP, we suggest to use a trusted VPN server for access to the softswitch web interface.
Starting from Sippy 5.1 (or greater) there is a security feature that warns the softswitch operator (if he has permissions to edit the firewall rules) to allow access to the switch to known IP addresses, and deny access to any unknown IP address. The warning is controlled from the Security Alerts section in the IP Firewall Tool, based on the type of firewall (DB, SIP, SSH or Web). If an external firewall is used the warning can be disabled by removing the selection from checkbox:

More information regarding IP Firewall setup could be found here:
https://support.sippysoft.com/a/solutions/articles/3000093126
Audit log tool
Audit log is a subsystem that records events on the Softswitch, with ability to filter by name/type/date.
More information available here:
https://support.sippysoft.com/a/solutions/articles/3000117512
How to setup an external firewall with Sippy Software:
External Firewall setup for use with Sippy SoftswitchMulti Factor Authentication:
For details on how Multi Factor authentication works please view the following support article:
Multi Factored Authentication (web users)